The Internet was created to share information. As the use of the internet has increased to include e-commerce and business software, it has become clear that not all information is intended to be shared with everyone. As more data became available, industries such as Financial Services, Health Care, and the Public Sector began to adopt laws to regulate the way sensitive data was handled and accessed. In other words, to prevent abuse of patients, customers, and financial information, companies began to build walls around their data.
Because of these compliance requirements, companies in regulated industries, and even some companies that have developed their own internal management systems, are striving to take advantage of the speed and innovation introduced by cloud computing.
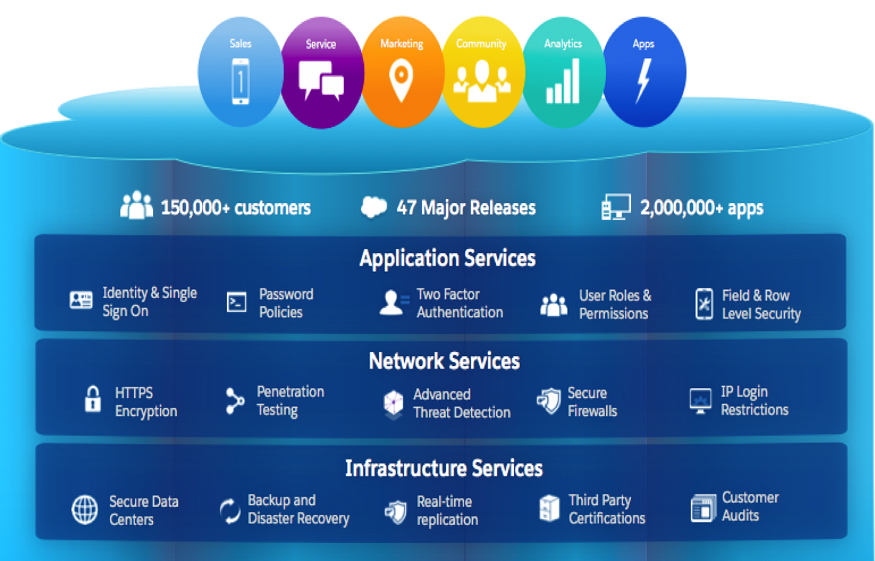
Trust Services for all Salesforce customers
At Salesforce, Trust is our # 1 value. We work behind the scenes to ensure that all customers have the highest level of data protection, availability, and performance. From two-factor authentication to strict password policies, all customers gain access to the same credentials of loyalty in our forum. Regardless of size, each Salesforce customer benefits from IP login restrictions, login history, fine-grained sharing, and test testing settings to see what changes Managers are making. If you need help in implementing Salesforce, you can always hire a best Salesforce Consultant.
Compliance with Regulated Industries
Although Trust Services provides what most customers need, some companies in the regulated industry have compliance requirements that go this way. Asset management firms, for example, need to track whether sensitive customer account data is being sent. Pharmaceutical companies that use clinical trials in Sales Cloud need to keep track of patient data tests to protect the integrity of clinical test results. Health insurance companies may require encryption of sensitive Protected Health Information, or PHI, so only medical providers can view the information, but all team members, such as Customer Service representatives, can continue to use the app’s core functions such as search, workflow and verification rules. , to help customers. Communication firms may need to encrypt sensitive PII, or Personal Information, as well as customer call data from Service Clouds. For these companies measuring rapid change in cloud infrastructure and meeting compliance requirements has been a challenge, to this day.
Introducing the Salesforce Shield
To help customers with complex management and compliance requirements, we are launching the Salesforce Shield, a premium set of natively integrated integration services on the Salesforce1 Platform. Salesforce Shield allows customers to see who is doing with sensitive data, know the status and value of their data going back ten years, and encrypt sensitive data at rest, while maintaining business performance. It is transparent and can be set in the afternoon with pointing and click tools. Salesforce Shield covers three key services:
Customers simply access the standard csv file via the API and drag the data to any number of viewing tools. Then, they can track when someone prints a page or list view, edits a record or old one, changes ownership, updates a list, or even when a user submits account data.
Field Audit Trail gives customers a timeline so they can go back and see the status and value of their data at any date, at any time. Expands what is now available with Field History Retention, providing customers with 10 years of tracking data for up to 60 field per item. The Field Audit Trail is built on a large data center that allows for great scaling and allows customers to access survey data in just two minutes.
Platform Encryption allows customers to encrypt sensitive data at rest while maintaining important functionality of the application. Because data is encrypted on a metadata layer on a website, a Salesforce application function key can be made ‘aware of encryption’ and work in spite of data encryption. Surprisingly, AppExchange partner apps, such as Conga, can re-enter and respect the data the customer chooses to encrypt in his or her organization. Platform Encryption is traditionally built on the platform and can be set up in just minutes.